30+ pages how to detect brute force attack using wireshark 3.4mb. A brute force attack is a trial and error method used to discover a password by systematically trying every possible combination of letters numbers and symbols until the correct combination is found. Some brute force attacks utilize dictionary words and lists of common passwords in order to. This video is relevant to my comprehensive course on Ethical Hacking. Read also attack and understand more manual guide in how to detect brute force attack using wireshark When you suspect a brute-force on the network follow these steps to locate it.
This alert detects brute force attacks performed either horizontally with a small set of passwords across many users vertically with a large set of passwords on just a few users or any combination of the two options. The alert is based on authentication events from sensors running on domain controller and AD FS servers.
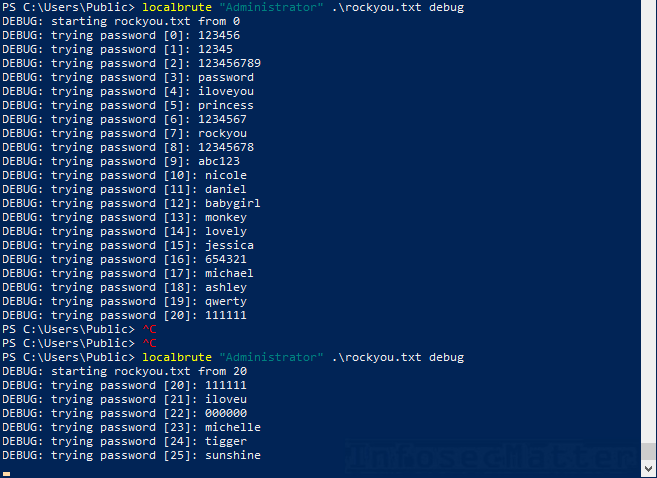
Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter
| Title: Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
| Format: eBook |
| Number of Pages: 224 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: March 2017 |
| File Size: 1.35mb |
| Read Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
 |
Brute-forcing is a method that tries a combination of numbers lowercase and uppercase letters and special characters to crack a password.

Brute-forcing is a method that tries a combination of numbers lowercase and uppercase letters and special characters to crack a password. In this lecture we shall learn how to use Wireshark to detect ARP Poisoning attacks and other suspicious activities in the network we will also learn how to protect against ARP Poisoning attacks. If the host is exposed directly to the Internet WAN and SSH service is running on the host it becomes a subject of constant brute force attacks performed by automated scripts like hydra. To detect SSH brute force attempts on systems running systemd service manager CentOS7Fedora21RHEL7 you can use journalctl command with parameters. In this video you will use a DomainPasswordSpray PowerShell script to perform a password spray attack on Active Directory. A credential-stuffing attack could try to breach a single user or many at once.
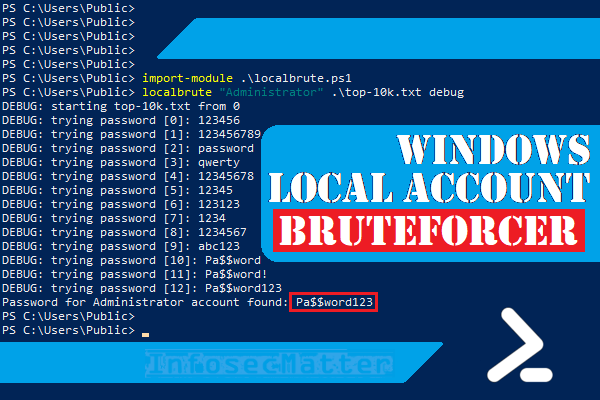
Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter
| Title: Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
| Format: ePub Book |
| Number of Pages: 187 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: November 2017 |
| File Size: 1.9mb |
| Read Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
 |

The Reaver Tool Running A Brute Force Attack Against The Wps Passcode Download Scientific Diagram
| Title: The Reaver Tool Running A Brute Force Attack Against The Wps Passcode Download Scientific Diagram |
| Format: PDF |
| Number of Pages: 160 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: June 2021 |
| File Size: 800kb |
| Read The Reaver Tool Running A Brute Force Attack Against The Wps Passcode Download Scientific Diagram |
 |

Brute Force Dictionary Attack Example Stack Overflow
| Title: Brute Force Dictionary Attack Example Stack Overflow |
| Format: ePub Book |
| Number of Pages: 339 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: October 2020 |
| File Size: 725kb |
| Read Brute Force Dictionary Attack Example Stack Overflow |
 |

Hydra Post Brute Force For Success Information Security Stack Exchange
| Title: Hydra Post Brute Force For Success Information Security Stack Exchange |
| Format: ePub Book |
| Number of Pages: 228 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: July 2021 |
| File Size: 810kb |
| Read Hydra Post Brute Force For Success Information Security Stack Exchange |
 |

Hydra Post Brute Force For Success Information Security Stack Exchange
| Title: Hydra Post Brute Force For Success Information Security Stack Exchange |
| Format: PDF |
| Number of Pages: 334 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: November 2018 |
| File Size: 725kb |
| Read Hydra Post Brute Force For Success Information Security Stack Exchange |
 |
Preventing Brute Force Attack Work Projects Work Simulation Tools
| Title: Preventing Brute Force Attack Work Projects Work Simulation Tools |
| Format: eBook |
| Number of Pages: 335 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: March 2020 |
| File Size: 3.4mb |
| Read Preventing Brute Force Attack Work Projects Work Simulation Tools |
 |
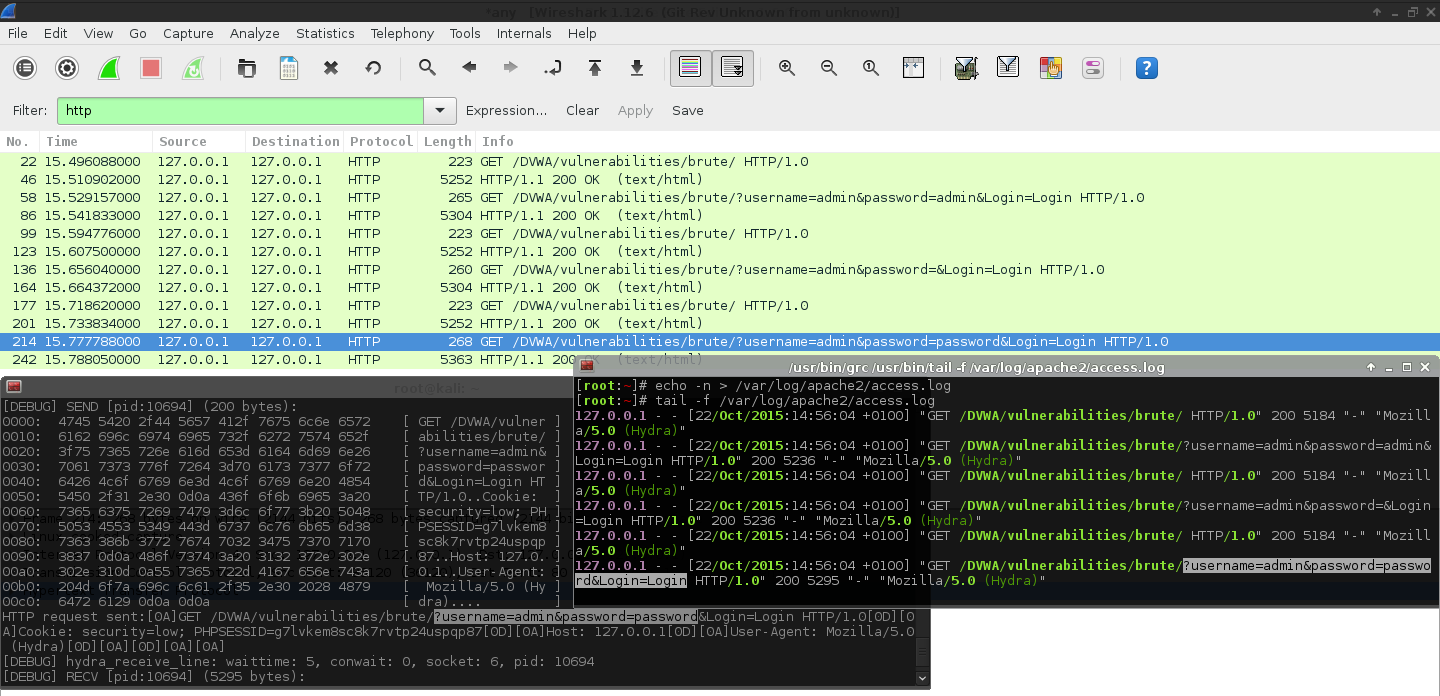
Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k
| Title: Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k |
| Format: ePub Book |
| Number of Pages: 133 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: April 2018 |
| File Size: 800kb |
| Read Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k |
 |
Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k
| Title: Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k |
| Format: ePub Book |
| Number of Pages: 206 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: October 2021 |
| File Size: 1.8mb |
| Read Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k |
 |

Detect Password Cracking Attempts Wireshark Work Security
| Title: Detect Password Cracking Attempts Wireshark Work Security |
| Format: PDF |
| Number of Pages: 297 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: July 2021 |
| File Size: 1.7mb |
| Read Detect Password Cracking Attempts Wireshark Work Security |
 |

Brute Force Dictionary Attack Example Stack Overflow
| Title: Brute Force Dictionary Attack Example Stack Overflow |
| Format: PDF |
| Number of Pages: 214 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: September 2021 |
| File Size: 3.4mb |
| Read Brute Force Dictionary Attack Example Stack Overflow |
 |

Detect Smb Brute Force Extrahop Munity Forums
| Title: Detect Smb Brute Force Extrahop Munity Forums |
| Format: eBook |
| Number of Pages: 245 pages How To Detect Brute Force Attack Using Wireshark |
| Publication Date: December 2018 |
| File Size: 1.7mb |
| Read Detect Smb Brute Force Extrahop Munity Forums |
 |
In this lecture we shall learn how to use Wireshark to detect ARP Poisoning attacks and other suspicious activities in the network we will also learn how to protect against ARP Poisoning attacks. Since no security measure can guarantee that an attacker will not succeed eventually intrusion detection techniques should be applied to detect. Connect Wireshark with port mirror to the port in the server that you suspect is under attack.
Here is all you need to learn about how to detect brute force attack using wireshark Ubuntu or Windows 2 nos 2. We will discover how to detect a. Look in Wireshark for unusual numbers of SSH login attempts whether or not they are successful. Preventing brute force attack work projects work simulation tools hydra post brute force for success information security stack exchange detect smb brute force extrahop munity forums dvwa brute force low level get form hydra patator burp g0tmi1k hydra post brute force for success information security stack exchange windows local admin brute force attack tool localbrute ps1 infosecmatter This can be performed using certain tools such as Brutus THC Hydra Medusa Burp Suite intruder and many other tools available online.


0 Comments